In the cryptocurrency world, a protocol is more than just technical jargon. Protocols form the foundation that makes cryptocurrencies work. You can think of them like traffic laws. In crypto, protocols are the rules that let the blockchain work safely, fairly, and without a central authority.
Protocols define how data is shared, verified, and recorded on the blockchain. Without protocols, there is no way to ensure that everyone is playing fair on the network.
What Is a Crypto Protocol?
A crypto protocol is a set of rules encoded into a blockchain that governs how the network operates. The rules define how data is transmitted, how transactions are validated, how participants reach agreements (called consensus) on the state of the network, and more. In other words, protocols are what make cryptocurrencies secure, transparent, and above all, decentralized.
Why are Protocols Important in Blockchain?
The basic concept of crypto protocols is quite simple. Without protocols, blockchains won’t exist. Protocols are what allow:
- Decentralization: No middlemen or banks. Just code.
- Security: Only the valid transactions get through.
- Consistency: Every copy on the blockchain is synchronized.
- Interoperability: Some protocols help different blockchain networks talk to each other
Just imagine hundreds of people writing the same book, all simultaneously. Protocols are the editors who make sure every version of the book is consistent. They allow users to trust the system without needing to trust each other. This is the power of the blockchain, and it all depends on protocols.
What are the Key Components of Crypto Protocols?
Crypto protocols are made up of different parts that work together to keep the blockchain running smoothly. The core components that most protocols rely on include:
Network Layer
The network layer is how the blockchain talks to itself. It defines how the nodes (computers in the network) connect and share data. It lets blocks, transactions, and updates move from one point to another quickly and securely.
The key functions of the network layer are:
- Peer Discovery (Finding other computers)
When a new computer (node) joins the blockchain, it needs to find other nodes to connect with. The network layer helps it do that.
- Data Propagation (Spreading the word)
When someone makes a transaction or creates a new block, the network will spread that information to all other computers.
- Broadcasting (Sharing transactions and blocks)
The network layer sends out new transactions and blocks so every node stays up to date.
- Network Integrity (Keeping everyone in sync)
The layer helps ensure that all data, such as transactions and blocks, is delivered quickly and reliably so that all nodes remain up to date with the latest version of the blockchain.
Consensus Mechanism
The consensus mechanism is how everyone agrees on what is true on the blockchain. Every blockchain needs a way to make sure all nodes agree on the current state of things. This is where consensus comes in.
Whether it is Proof of Work (like Bitcoin), Proof of Stake (like Ethereum), or one of the many other methods used today, consensus mechanisms keep the blockchain synchronized and secure. They also prevent double-spending and keep the chain trustworthy.
Transaction Validation
Anything that gets added to the blockchain needs to be validated first. Transaction validation is the process of making sure everything is legit. This includes:
- Verifying digital signatures to confirm the sender is who they say they are.
- Checking balances to ensure the sender has enough funds.
- Following protocol rules like transaction size limits or correct formatting
All of this is done using advanced cryptographic techniques.
Take, for instance, Bitcoin. In Bitcoin, every transaction must be signed using a private key. Nodes then verify the signature using the sender’s public key. They also check the UTXO set (unspent transaction outputs) to confirm the sender has the coins they are trying to spend.
If the sender’s signature is valid, they own the amount and pay the required fee, and as long as the transaction format is correct, the transaction will go through. Then it can be added to a block by a miner (in PoW) or a validator (in PoS).
If any of these rules are not followed, the transaction won’t go through.
In September 2023, Bitcoin mining firm Marathon Digital mined an invalid block (block height 809,478) due to a transaction ordering issue. Specifically, the transaction attempted to spend an input from another transaction that was included later in the block. This violated the network’s protocol rules.
Smart Contracts
Smart contracts are programs that run on the blockchain. They let users do more than just send money. You can use them to set up rules, automate actions, and build things like DeFi apps and games. Once a smart contract is deployed, it will run exactly as it is written, without a middleman or manual approvals.
Types of Crypto Protocols
Blockchain technology is complicated and incredibly diverse. Different crypto protocols exist to serve different purposes. Some are built for just simple transactions, whereas others are designed to enable complex operations through smart contracts.
Each type of protocol has a specific job. Below, you will find the main types of crypto protocols and learn how they work.
Payment Protocols
Payment protocols handle peer-to-peer transfers of digital money without the need for a middleman. The goal is to move the crypto value from one person to another, safely and efficiently.
Example: Bitcoin uses a payment protocol that validates every transaction through its blockchain. It checks digital signatures and balances before it confirms a transaction. Once it is verified, it will be added to the ledger forever.
Smart Contract Protocols
Smart contract protocols let you write and run code on the blockchain. The code runs automatically when all conditions are met, without the need to involve a third party. This enables a massive amount of utility, and it acts as the foundation for the entire decentralized finance (DeFi) ecosystem.
Example: Ethereum made smart contracts popular on the crypto market by introducing Turing-complete functionality via the Solidity programming language in 2015. This innovation laid the foundation for decentralized applications (dApps), DeFi protocols, non-fungible tokens (NFTs), and even decentralized autonomous organizations (DAOs).
Today, they are used in many blockchains, including Solana, Avalanche, and Polkadot, to mention a few.
Privacy Protocols
Most blockchains focus on transparency, but others have built privacy protocols to protect the user’s identity. Privacy protocols are focused on making transactions confidential, hiding amounts and sometimes even identities.
Example: Monero uses stealth addresses and ring signatures to hide who sent or received funds. Zcash uses a cryptographic method called zk-SNARKs to protect transactions so nobody can trace them, not even on the public ledger.
Consensus Protocols
Consensus protocols are how all the computers or nodes agree on what is true in the blockchain. Based on this, there are numerous types of consensus protocols in the crypto industry. They differ based on the approach to validating transactions and securing the blockchain network. Here is a breakdown of the most prominent consensus protocols on the market:
| Consensus Mechanism | How It Works | Used By |
| Proof of Work (PoW) | Miners solve complex puzzles. The first to solve adds the next block and earns crypto. | Bitcoin, Litecoin |
| Proof of Stake (PoS) | Validators are chosen based on the amount of crypto they stake as collateral. | Ethereum (post-merge), Cardano |
| Delegated Proof of Stake (DPoS) | Token holders vote for a few delegates who then validate transactions. | EOS, Tron, Tezos |
| Proof of Authority (PoA) | Pre-approved and known authorities validate transactions. | VeChain, Liquid (Blockstream) |
| Proof of Burn (PoB) | Users destroy (burn) crypto to gain the right to validate transactions. | Slimcoin, Koinos |
| Proof of History (PoH) | Builds a historical timeline to verify when events occurred. | Solana |
Interoperability Protocols
Interoperability protocols, sometimes called cross-chain protocols, let different blockchains “talk” to each other. Without them, blockchains are like separate islands. They work well on their own, but they cannot communicate.
These protocols enable data and asset transfers across different networks.
Example: Polkadot uses its Relay Chain to connect multiple blockchains (called parachains). This creates an entire ecosystem of interoperable chains.
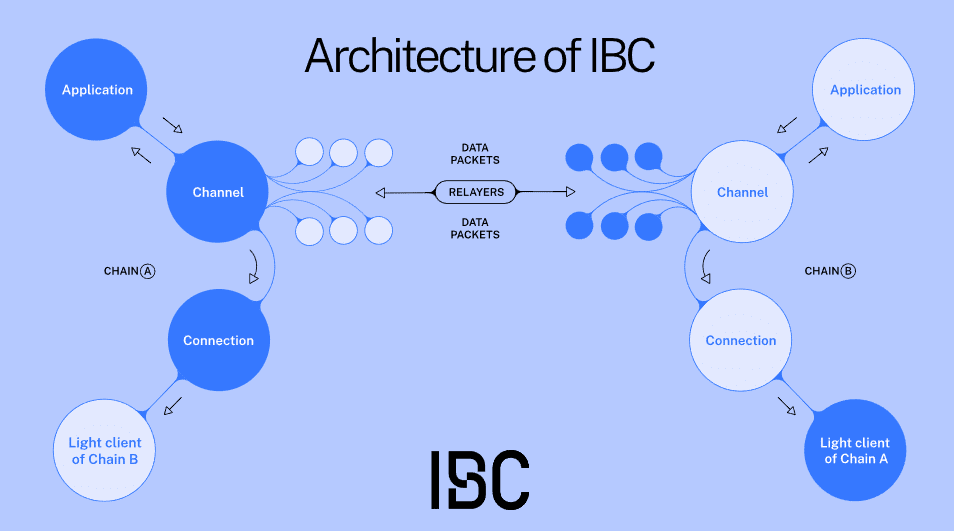
Cosmos uses the Inter-Blockchain Communication (IBC) protocol to do something similar. IBC allows tokens and data to move freely between different compatible blockchains.
Governance Protocols
Governance protocols decide how decisions are made on the blockchain. Who votes on the changes? Who upgrades the system? The rules are set in the governance protocol.
Example: DAOs (Decentralized Autonomous Organizations) are a popular governance mode used in many different blockchains. The token holders propose and vote on changes like adjusting fees, approving new features, and more.
Token Protocols
Token protocols define how digital tokens are created, used, and transferred between network participants. They set the rules for tokens on the blockchain. This ensures tokens can work across wallets, apps, and crypto exchanges.
Example: ERC-20 is Ethereum’s most common token standard. It powers tens of thousands of tokens like USDT, Chainlink, and Uniswap. Without a standard like ERC-20, every token would need custom code and wouldn’t be compatible across different tools.
Other popular token protocols include:
- ERC-721: Used for non-fungible tokens (NFTs)
- ERC-1155: Supports NFTs and fungible tokens in a single contract
- BEP-20: Binance Smart Chain’s version of ERC-20
- SPL Tokens: Solana’s native token standard
- TRC-20: Tron’s equivalent of ERC-20 for fungible tokens
How Crypto Protocols Evolved
Crypto protocols have come a long way since Bitcoin was launched in 2009. It all started as a simple system for peer-to-peer payments and has grown into a much more complex ecosystem that powers DeFi, smart contracts, governance models, cross-chain interoperability, and more.
Over time, developers have created innovations to find scalability solutions, reduce costs, and simply make blockchain technology more adaptable and user-friendly. Let’s see how crypto protocols evolved over time.
Layer 1 vs. Layer 2 Protocols
Layer 1 (L1) protocols are the foundational blockchains that handle all core functions like security, consensus, and transaction validation. Examples of L1 protocols include Bitcoin, Ethereum, and Solana.
Layer 2 (L2) protocols are solutions built on top of Layer 1 blockchains to boost scalability and reduce transaction fees. They process transactions off-chain and then report back to the main chain.
Examples include Optimism, Arbitrum, and the Lightning Network for Bitcoin.
Modular vs. Monolithic Protocol Design
Monolithic blockchains handle all blockchain functions, such as execution, consensus, and data availability within a single layer. Examples of such blockchains include Ethereum and Solana.
Modular blockchains separate blockchain functions across different layers or modules, which allows for greater scalability and more flexibility. One example of this is Celestia.
On-Chain Governance and Protocol Upgrades
On-chain governance allows stakeholders to participate directly in protocol decisions through voting mechanisms.
Ethereum, for instance, implemented significant upgrades like the transition to Proof of Stake through community consensus and Ethereum Improvement Proposals (EIPs).
Uniswap utilizes a decentralized autonomous organization where UNI token holders can vote on protocol changes and treasury allocations.
Tokenomics and Incentive Structures
Tokenomics involves designing economic incentives to encourage the desired behaviors within the blockchain ecosystem. Properly aligned incentives can promote user participation and network security.
Poorly designed tokenomics, on the other hand, can lead to devastating issues like inflation. Take, for instance, the Terra/LUNA ecosystem, which faced a significant crash because of unsustainable and ineffective incentive mechanisms.
Interoperability and Cross-Chain Protocols
As the blockchain ecosystem grows, interoperability becomes vital for better interaction between different networks.
Some examples of this include:
- Polkadot uses a relay chain to connect different parachains and facilitate cross-chain interoperability.
- Cosmos employs the IBC protocol to enable data and asset transfers between different blockchains.
- Chainlink CCIP provides a decentralized protocol for communication across chains.
Notable Crypto Protocols
The crypto ecosystem is built on a range of protocols. Each of the blockchain protocols comes with its own set of rules, purpose, and approach to decentralization. These protocols define how the networks operate. That being said, below are some of the most influential crypto protocols that have shaped the industry to date.
Bitcoin Protocol
Bitcoin was the first cryptocurrency, introduced as a decentralized alternative to traditional financial systems. Created in January 2009 by the pseudonymous Satoshi Nakamoto, Bitcoin set the foundation for all blockchain-based technologies that followed.
The very first Bitcoin block, known as the “Genesis Block,” was mined on January 3, 2009. The block reward was initially 50 BTC, though it is halved approximately every four years. The maximum supply of Bitcoin is capped at 21 million coins.
Key features
Consensus mechanism: Proof of Work (PoW)
Main use: Peer-to-peer digital cash
Immutability: All transactions, once confirmed, are permanent and public
Security: A global network of miners maintains the network
How the protocol works
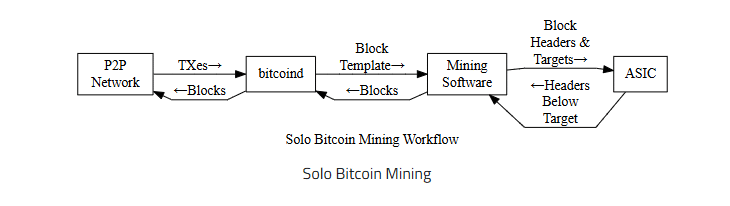
When you send 0.5 BTC, the protocol will ensure you have sufficient balance. It will then validate your digital signature and broadcast it. Next, miners compete to add it to the blockchain. Miners compete to solve SHA-256 puzzles. The first to solve gets to add a block and receive BTC as a reward.
Ethereum Protocol
Ethereum introduced smart contracts, the programmable scripts that automatically execute based on conditions. The Ethereum whitepaper, released in late 2013 by Vitalik Buterin, laid out a “world computer” concept.
Ethereum is a decentralized, open-source blockchain that enables smart contracts and decentralized applications. It was officially launched in July 2015 by Buterin and his partners (including Gavin Wood, Joseph Lubin, Charles Hoskinson, etc.). Today, the Ethereum Virtual Machine (EVM) executes smart contracts across thousands of nodes.
Key features
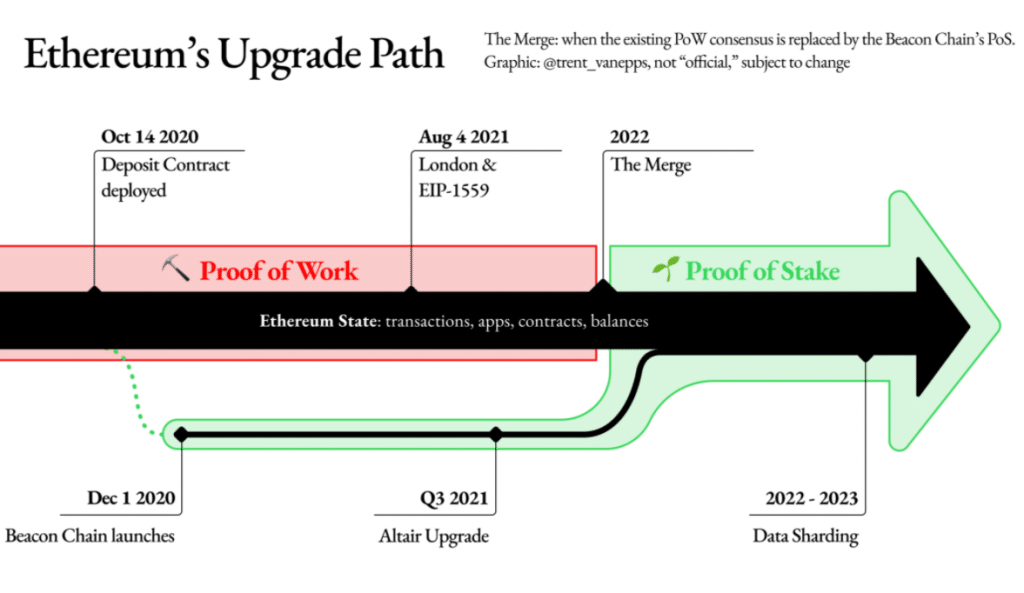
Consensus mechanism: Proof of Stake (since “The Merge” from September 2022)
Main use: Decentralized finance and smart contracts
Immutability: Transactions and contract interactions are recorded permanently on the blockchain
Security: Stakers and validators secure the network using ETH deposits
How the protocol works
When a user interacts with a DApp, Ethereum will use the EVM to simulate and verify their transaction. Validators confirm that the sender has enough ETH, that the predefined rules are followed, and that gas fees are covered.
If all checks pass, the transaction is added to the block and finalized via PoS.
Cardano Protocol
Cardano is a proof-of-stake blockchain launched in September 2017 by Charles Hoskinson, a co-founder of Ethereum. He built the network through peer-reviewed research and turned it into a widely popular approach to blockchain design.
Cardano uses a layered architecture. Its native coin, ADA, is now used for staking, governance, and smart contract interactions.
Key features
Consensus mechanism: Ouroboros (Proof of Stake)
Main use: Smart contracts and secure value transfer
Immutability: Transactions are validated and permanently recorded
Security: Based on mathematical proofs and Haskell codebase
How the protocol works
ADA holders can stake coins in a pool. In each time period (also known as epoch), the protocol will select “slot leaders” to validate blocks. When you send ADA, the system will check your balance and your signature, then include it in a block proposed by a slot leader. The transactions are validated by the Ouroboros protocol and added to the chain.
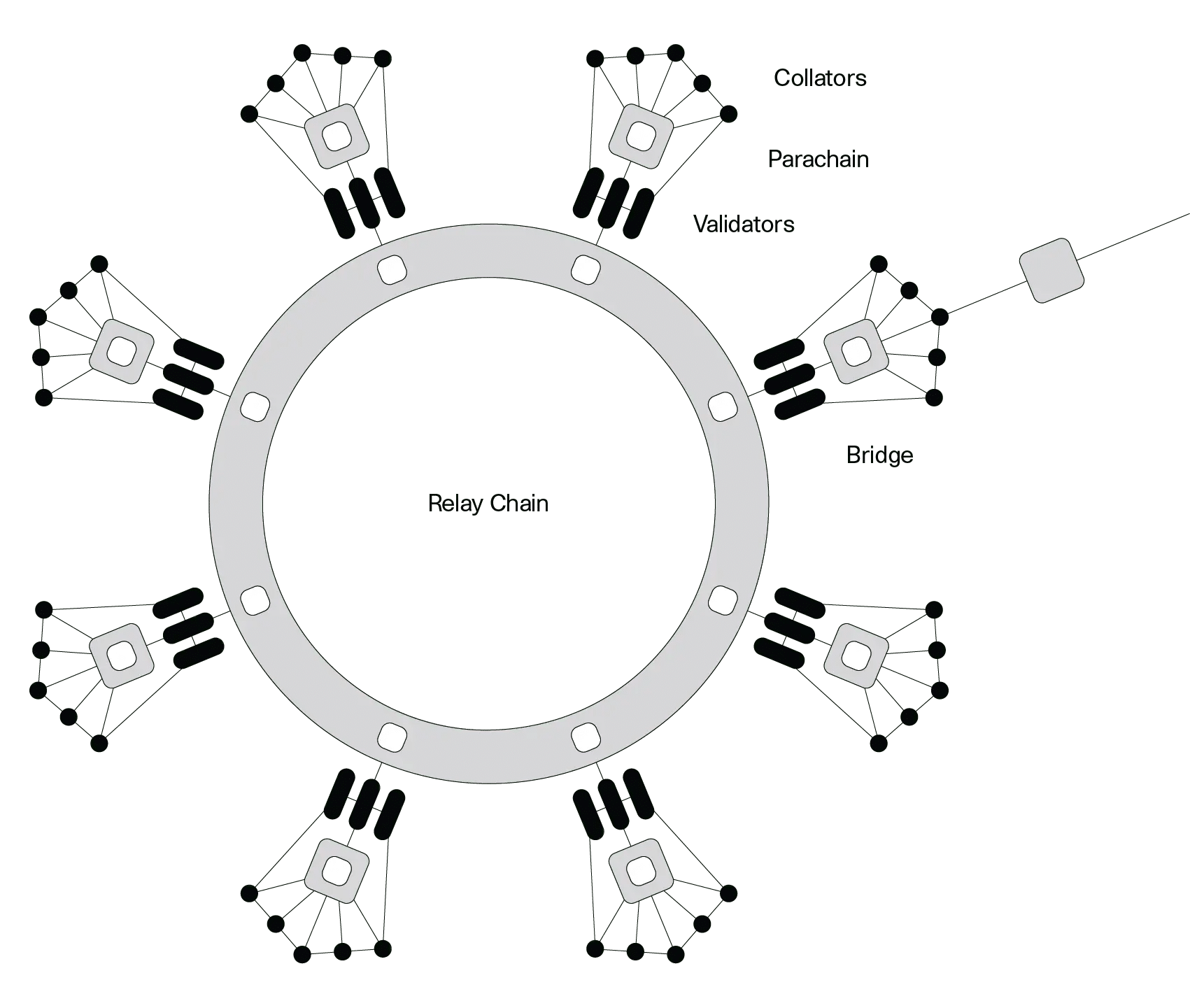
Polkadot Protocol
Polkadot is a multi-chain protocol launched in May 2020. It was founded by Dr. Gavin Wood, another co-founder of Ethereum. Its purpose is to connect multiple blockchains, allowing them to communicate easily and share security.
Polkadot introduces parachains, which are custom blockchains connected to a central Relay Chain. The chains can interact and transfer data with each other securely.
Key features
Consensus mechanism: Nominated Proof of Stake (NPoS)
Main use: Cross-chain interoperability, custom blockchain development
Immutability: Parachains finalize blocks through Relay Chain validators
Security: Shared security across parachains via the Relay Chain
How the protocol works
When a user interacts with a DApp on a parachain like Moonbeam, the transaction is verified locally. Once this is done, the transaction is passed through the Relay Chain for finalization. Validators on the Relay Chain confirm the block, and data is transferred across them using XCM (Cross-Consensus Messaging).
Conclusion
Blockchain protocols are the core of blockchain technology. They define how transactions are validated, how blocks are created, and how network participants reach consensus without relying on a central authority. These rules are what make decentralized networks a possibility.
Whether it’s Bitcoin’s protocol for secure peer-to-peer payments or Ethereum’s infamous smart contracts, every action on a blockchain follows a protocol. This is why understanding crypto protocols is critical if you want to work in this space, regardless of whether you are a developer, investor, or casual user.
FAQs
What is a crypto protocol, and how does it work?
A crypto or blockchain protocol is a set of rules that govern how data is shared and validated in a decentralized network. The protocol outlines how nodes interact and reach consensus, as well as how they maintain security.
What is the role of smart contracts in crypto protocols?
Smart contracts are self-running pieces of code built into the blockchain protocols. They execute automatically when the conditions are met.
How do Layer 1 and Layer 2 protocols differ?
Layer 1 protocols are the base blockchains, like Bitcoin and Ethereum. Layer 2 protocols are built on top of them to boost their speed and lower fees.
What are some examples of popular crypto protocols?
Some major crypto protocols include the Bitcoin Protocol, Ethereum Protocol, Cardano Protocol, and Polkadot Protocol.
What are the security risks of crypto protocols?
If a protocol has bugs or poor design, attackers could exploit it. The most common risks include attacks, smart contract vulnerabilities, and flawed consensus mechanisms.
Are different blockchain protocols interoperable?
Some are, some are not. Projects like Polkadot and Cosmos are working to make blockchain protocols talk to each other, allowing data and assets to move across chains.
What is a token standard?
A token standard is part of the blockchain protocol that defines how tokens behave. For instance, ERC-20 on Ethereum sets rules for how tokens are stored.
How are updates or forks implemented in blockchain protocols?
Protocols are updated through forks. A hard fork creates a new version of the blockchain, such as Bitcoin vs. Bitcoin Cash. A soft fork adds new features but stays compatible with the old rules.
References
- Bitcoin Recent Hiccup: Understanding the Invalid Block – Bitcoinist
- What Are ZK-SNARKs – Z.Cash
- Polkadot Chain Overview – Polkadot
- IBC-Go Documentation – IBC Cosmos
- What Is ERC-20 – CoinMarketCap
- Ethereum: How Does It Work and What Are Its EIPS – CryptoforInnovation
- Why Tokenomics Models Fail – Forbes
- Bitcoin Developer Guide – Bitcoin
- The Ethereum Merge – Ethereum
- Ethereum’s Upgrade Path – Pintu Academy
- Cardano Network Docs – Cardano
- Ouroboros Protocol – IOHK

