Bitcoin is an entire system containing multiple elements that collectively enable peer-to-peer electronic transactions without intermediaries. This system combines cryptography, distributed computing, economic incentives, and consensus mechanisms to create a financial network that has remained secure and operational for over a decade and a half.
Bitcoin was introduced in 2009 by a pseudonymous creator known as Satoshi Nakamoto, ushering in a new era of economic disruption. As the world’s first successful decentralized digital currency, Bitcoin operates without central control from governments, banks, or institutions. Instead, it functions through a complex system of components working in harmony to maintain security, transparency, and reliability.
In this article, we offer a complete Bitcoin system overview, from the foundational software and protocol to the complex network of nodes, miners, and users that bring it to life.
Key Takeaways
- Bitcoin is a complete system that combines open-source software, cryptographic security, a global network of nodes, and economic incentives to enable decentralized finance without intermediaries.
- The blockchain creates a publicly viewable yet secure record of all transactions. Each block is cryptographically linked to all previous blocks.
- Bitcoin faces a constant balancing act between scalability, security, and decentralization, with solutions developing on both the base layer and through Layer 2 technologies like Lightning Network.
The Definition of Bitcoin Software
Bitcoin software is open-source, meaning anyone can examine, modify, or contribute to its development. This approach ensures transparency and collaborative improvement.

Bitcoin Core
Bitcoin Core stands as the original and reference implementation of the Bitcoin protocol. First developed by Satoshi Nakamoto in 2009, this software client remains the most widely used version on the network. After Nakamoto’s departure in late 2010, a dedicated group of developers known as “core developers” took over the maintenance and development of the software.
What are the functions of the Bitcoin Core?
- It implements the Bitcoin protocol rules.
- It validates transactions and blocks.
- It maintains a complete copy of the blockchain.
- It connects to and communicates with other nodes.
- It provides wallet functionality for storing and managing bitcoins.
The software is regularly updated to improve performance, security, and functionality, with each update carefully reviewed by multiple developers to minimize vulnerabilities and bugs.
Alternative Implementations
While Bitcoin Core is the reference implementation, several alternative Bitcoin clients exist, including Bitcoin Knots, btcd, Libbitcoin, and Bitcoin Verde. These alternative Bitcoin implementations help maintain decentralization by preventing overreliance on a single code base while still following the same protocol rules.
Having multiple implementations is important because:
- It prevents a single bug from affecting all Bitcoin users
- It ensures no single development team controls the coin
- It provides options for different technical needs
- It verifies the protocol rules are correctly implemented
- It increases the network’s resilience against attacks
Bitcoin Protocol
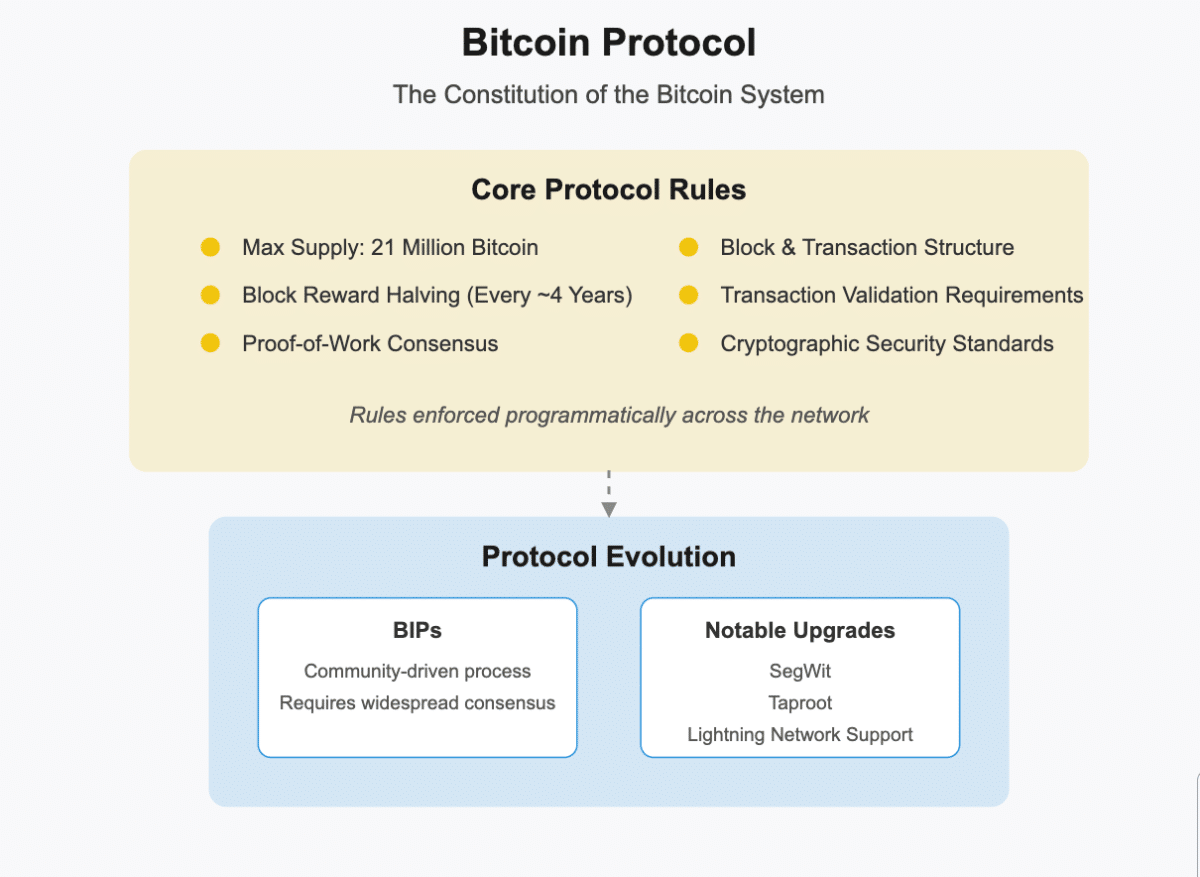
The Bitcoin protocol defines the fundamental rules for how the Bitcoin network operates. It’s essentially the constitution of the Bitcoin system—a set of standards and procedures that all participants must follow to remain part of the network.
There are several Bitcoin rules that need to be followed:
- The maximum supply (21 million).
- The block reward halving schedule (approximately every four years).
- The consensus mechanism based on proof-of-work.
- The structure of blocks and transactions.
- The validation requirements for transactions.
- The cryptographic standards for security.
These rules are expressed in code within the software rather than existing as a separate written document. This implementation ensures that the rules are enforced programmatically and consistently across the entire network. We will discuss these rules and concepts throughout the article.
Protocol Evolution
While the Bitcoin protocol’s core principles remain stable, it can evolve through proposals called Bitcoin Improvement Proposals (BIPs). These upgrades have to achieve widespread consensus among the Bitcoin community before implementation. This method creates Bitcoin’s decentralized governance model.
Notable protocol upgrades have included SegWit (Segregated Witness), Taproot, and Lightning Network compatibility, each strengthening Bitcoin’s functionality while maintaining backward compatibility.
Nodes in the Bitcoin Network
Nodes form the backbone of the Bitcoin network. A node is any computer running the Bitcoin software that connects to other computers in the network. These nodes collectively store, validate, and grow the blockchain, ensuring the network’s integrity and decentralization.
Full Nodes
Full nodes are the most comprehensive type of Bitcoin node. Full nodes download the complete Bitcoin blockchain (over 500GB) and verify all transactions themselves. They share valid transactions with other nodes and reject invalid ones.
Full nodes need substantial storage and processing power, but they also offer the best security and privacy while helping keep the network healthy.
Types of Nodes
Beyond standard full nodes, there are several specialized node types, and let’s have a look at them:
Light Nodes (SPV Nodes)
Lightweight nodes, also called SPV (Simplified Payment Verification) nodes, download only block headers rather than complete blocks. They verify transactions using a simplified method that requires far less storage and capability—just a few gigabytes instead of hundreds.
You’ll find these nodes commonly in mobile wallets and devices with limited resources. While they sacrifice some security and privacy, they offer much greater convenience for everyday users.
Mining Nodes
Mining nodes actively compete to create new blocks in the blockchain. They solve complex cryptographic puzzles and, when successful, earn both block rewards and transaction fees. Running a mining node requires additional mining software and typically uses specialized hardware called ASICs (Application-Specific Integrated Circuits) designed specifically for Bitcoin mining.
Pruned Nodes
These nodes store the complete blockchain initially but later delete older blocks to save disk space while still maintaining recent blockchain data and verifying the entire blockchain when synchronizing.
Archival Nodes
Archival nodes store the complete blockchain history, including all transaction data, supporting services like block explorers that need historical data access. They require the most storage space of all node types.
The diversity of Bitcoin nodes allows users with different resources and needs to participate in the Bitcoin network according to their capabilities, and all this while maintaining the network’s decentralized nature.
The Blockchain
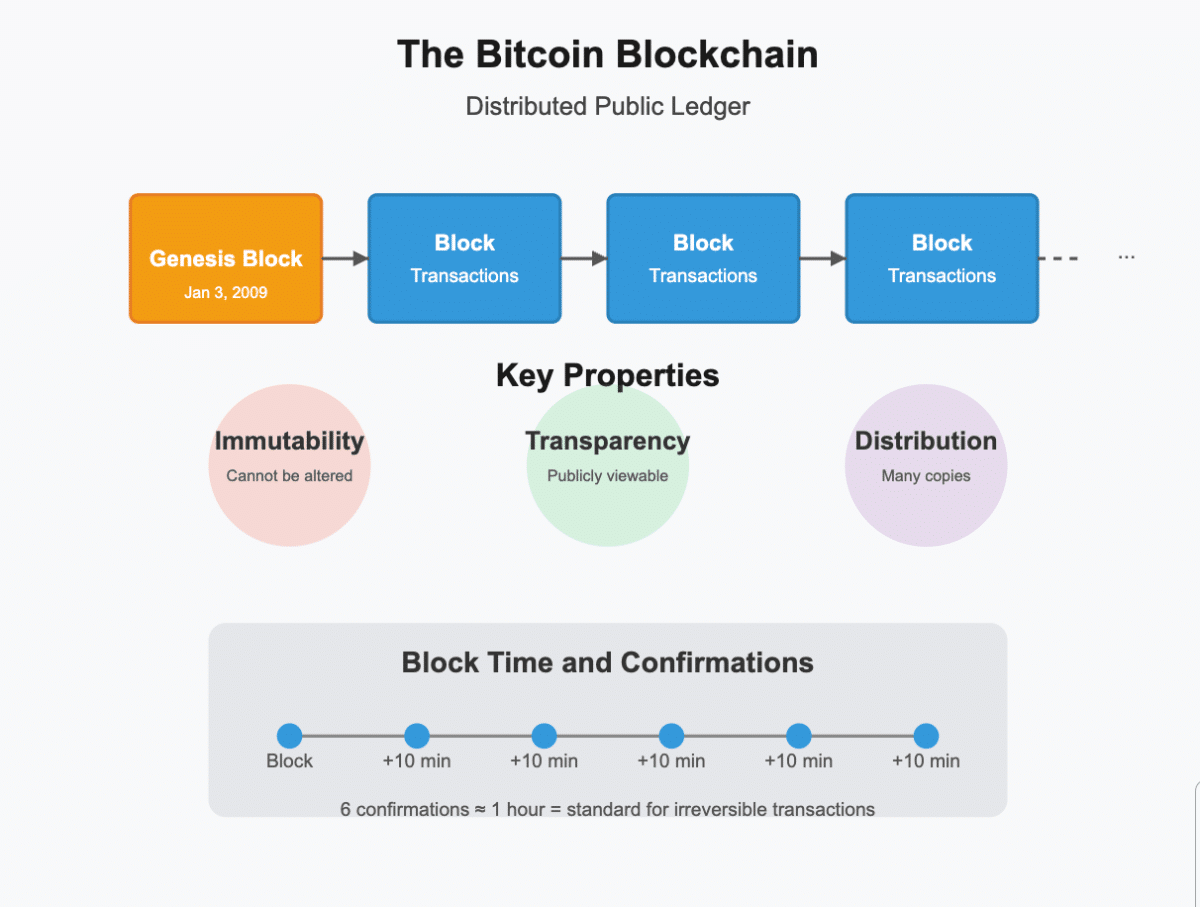
The blockchain is the distributed public ledger that is Bitcoin’s foundational data structure. It chronologically records all Bitcoin transactions that have ever occurred in a continuous chain of blocks.
The Bitcoin blockchain consists of a series of blocks, each containing a block header with metadata, a reference to the previous block (creating the “chain”), a bundle of transactions, and a proof-of-work solution. Each block builds upon the previous one, creating an unbroken chain that extends back to the “genesis block” mined by Satoshi Nakamoto on January 3, 2009.
Key Properties
The blockchain design provides several critical features:
Immutability
Once transactions are confirmed and buried under subsequent blocks, they become extremely difficult to alter. This comes from the proof-of-work system, where changing any information in a block would require redoing the computational work for that block and all subsequent blocks. This task becomes more difficult as the chain grows longer.
Transparency
The entire blockchain is publicly accessible. Anyone can view all transactions that have ever occurred on the Bitcoin network, creating unprecedented financial transparency. Let’s not forget that it still preserves user pseudonymity through cryptographic addresses.
Distributed Storage
The blockchain is not stored in a central location but is instead replicated across thousands of nodes worldwide. This distribution ensures that no single entity controls the ledger and that it remains available even if many nodes go offline.
Block Time and Confirmations
New blocks are added to the Bitcoin blockchain approximately every 10 minutes. When a block recording is complete and a transaction is included in a block, it receives one “confirmation.” Each subsequent block built on top adds another confirmation, with six confirmations (about one hour) traditionally considered the standard for irreversible transactions.
Mining and Proof of Work
Mining is the process by which new Bitcoins are created and transactions are confirmed on the network. It is both the security mechanism for the blockchain and the issuance system for new currency.
Bitcoin mining involves several steps:
- Miners collect unconfirmed transactions from the network.
- They organize these transactions into a block.
- They compute a cryptographic hash of the block header.
- They repeatedly modify a value in the header (the “nonce”) and rehash until finding a solution that meets the network’s difficulty target.
- When a valid solution is found, they broadcast the block to the network.
- Other nodes verify the solution and, if valid, add the block to their copy of the blockchain.
This process requires substantial computational power, as miners must perform trillions of hash calculations to find a valid solution.
Proof of Work
Proof of Work (PoW) is the consensus mechanism that secures the Bitcoin network. Miners must demonstrate they’ve expended computational resources by solving a difficult mathematical puzzle. The key properties of Bitcoin’s PoW include:
- Difficulty Adjustment: The network automatically adjusts the mining difficulty every 2,016 blocks (approximately two weeks) to maintain a 10-minute average block time
- Resource Intensity: The process intentionally requires significant computing power and electricity, making attacks economically costly
- Verifiability: While solutions are difficult to find, they’re easy for other nodes to verify
- Security Mechanism: The energy expenditure required makes it expensive to attack the network
Economic Incentives
Miners are motivated by two types of rewards – block rewards and transaction fees. With block rewards, the newly created Bitcoins are awarded to the miner who finds a valid block (currently 3.125 BTC per block as of the April 2024 halving).
With transaction fees, additional fees are attached after transaction validation processes that miners collect. These incentives create a self-sustaining security system where miners are economically motivated to protect the network integrity.
Mining Equipment
Bitcoin mining has evolved from CPU mining (personal computers) to specialized hardware:
- ASICs (Application-Specific Integrated Circuits): Custom chips designed solely for Bitcoin mining
- Mining Farms: Large-scale operations with thousands of ASICs
- Mining Pools: Collaborative efforts where miners combine their computing power and share rewards proportionally
Cryptographic Security
Cryptography is something that forms Bitcoin’s security model, enabling secure ownership, transfer, and verification of funds without trusted third parties.
Bitcoin uses public key cryptography (also known as asymmetric cryptography) to secure transactions:
- Private Keys: Secret numbers known only to the owner that are the ultimate proof of ownership for Bitcoins
- Public Keys: Derived from private keys and used to create Bitcoin addresses
- Digital Signatures: Created using private keys to authorize transactions without revealing the key itself
This system allows anyone to verify that transactions are authorized by the rightful owner of the funds while keeping the private keys secure.
Hash Functions
Bitcoin uses the SHA-256 cryptographic hash function extensively for transaction hashing, creating Merkle trees, proof of work calculations, and block chaining. Hash functions ensure data integrity and provide a way to efficiently verify large amounts of data.
Cryptographic Challenges
Bitcoin’s cryptographic security relies on several mathematical challenges, such as the Discrete Logarithm Problem, hash pre-image resistance, and collision resistance. These mathematical properties make it computationally impossible to break the Bitcoin security model with current technology, though advances in quantum computing may eventually pose challenges.
Wallets and Address Generation
Bitcoin wallets are software applications or hardware devices that manage the cryptographic keys needed to interact with the Bitcoin network. Despite the name, wallets don’t actually store Bitcoins—they store the keys that prove ownership of the coins recorded on the blockchain.
There are several types of Bitcoin wallets:
Software Wallets
Software wallets include desktop applications, mobile apps, and web-based wallets accessed through browsers. They offer convenience but can be vulnerable to online attacks.
Hardware Wallets
Physical devices designed to securely store private keys offline, such as Ledger, Trezor, and Coldcard. They provide enhanced security against online threats.
Paper Wallets
Physical documents containing printed private keys and QR codes that serve as a completely offline BTC storage option. They require careful handling to avoid damage or theft.
Brain Wallets
Private keys are derived from memorized passphrases. While theoretically secure if using strong passphrases, they’re generally not recommended due to vulnerability to brute force attacks.
Address Generation
Bitcoin addresses are created through a multi-step process that involves generating a private key, deriving the public key, creating a Bitcoin address by applying hash functions to the public key and formatting the address with Base58Check encoding. This process is a way of Bitcoin address generation that functions as the destination for receiving funds.
Hierarchical Deterministic (HD) Wallets
Modern Bitcoin wallets typically implement HD wallet technology (BIP32) which allows the generation of multiple private keys and addresses from a single seed, recovery of all addresses using only the seed phrase, and improved organization through hierarchical address structures. This technology improves backup and recovery procedures by requiring users to secure only a single seed phrase.
Bitcoin Transactions
Bitcoin transactions represent the transfer of value between addresses on the network. Each transaction consists of inputs (sources of Bitcoins) and outputs (destinations for Bitcoins).
Transaction Structure
A Bitcoin transaction contains several key components and let’s break them down below:
- Version Number: Indicates which rules this transaction follows
- Inputs: References to previous transaction outputs being spent
- Outputs: New unspent transaction outputs (UTXOs) created by this transaction
- Locktime: The earliest time or block when the transaction may be added to the blockchain
- Witness Data: (In SegWit transactions) Signature data separated from the main transaction
The UTXO Model
Bitcoin uses the Unspent Transaction Output (UTXO) model, where Bitcoins exist as “unspent outputs” from previous transactions. Each transaction consumes existing UTXOs as inputs and creates new UTXOs as outputs, with the difference between input and output values becoming the transaction fee. This model differs from the account-based model used in traditional banking.
Transaction Lifecycle
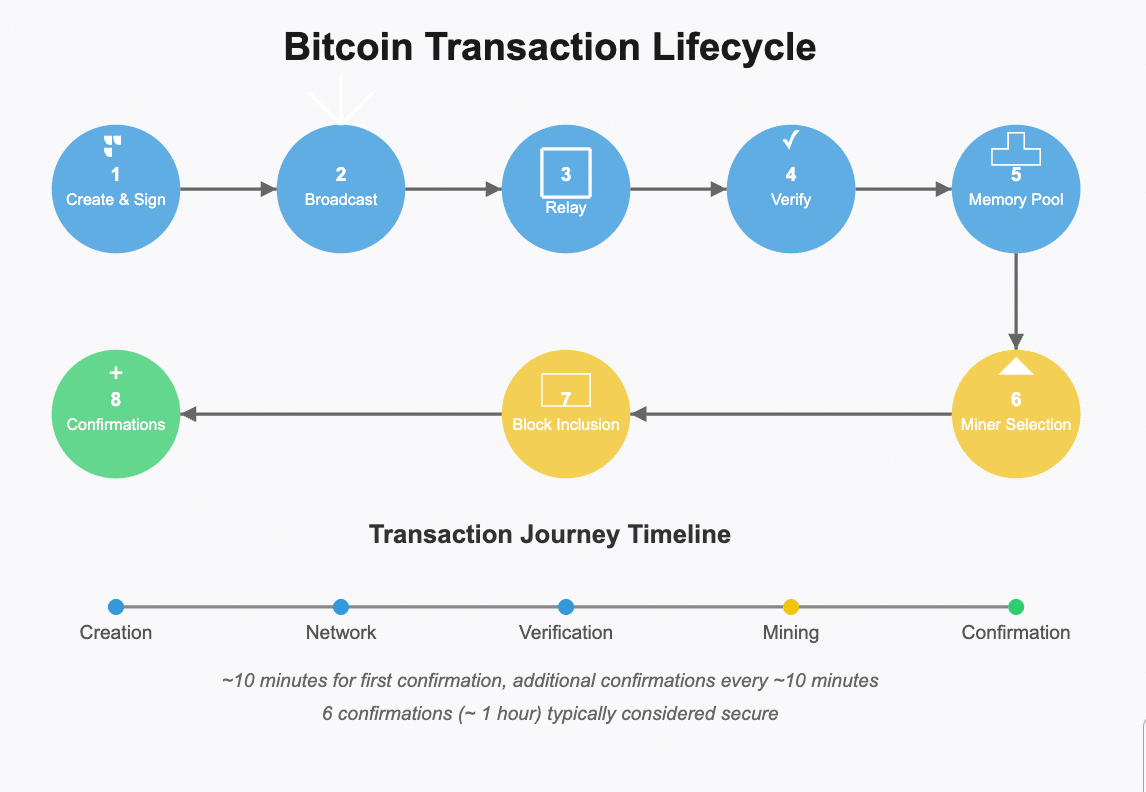
A transaction follows these steps:
- A wallet creates and signs a transaction
- The transaction is sent to the Bitcoin network
- Nodes relay the transaction to their peers
- Nodes verify the transaction’s validity
- Valid transactions enter the memory pool of pending transactions
- Miners select transactions from their mempool for inclusion in a block
- The transaction confirmation, it is included in a block
- Each subsequent block adds another confirmation
Transaction Types
Bitcoin supports several transaction types, including P2PKH (standard transactions), P2SH (script hash transactions), native and nested SegWit transactions, and the newest Taproot (P2TR) transactions with enhanced privacy and smart contract capabilities.
Consensus Mechanisms
Consensus mechanisms are the processes by which all nodes in the network achieve decentralized agreement on the state of the blockchain.. The Bitcoin consensus mechanism ensures that all participants have the same transaction history view without requiring central coordination.
Nakamoto Consensus
Bitcoin uses a consensus mechanism often called “Nakamoto Consensus,” combining Proof of Work with the longest chain rule, where nodes accept the blockchain with the most cumulative proof of work. This mechanism allows the network to achieve consensus even when some nodes are offline or malicious.
Achieving Network Agreement
The Bitcoin network consensus is maintained through independent verification of every transaction and block against protocol rules. Nodes automatically reject invalid transactions or blocks, ensuring compliance with network standards.
In the case of competing chains (forks), nodes follow the chain with the most cumulative work. Economic incentives strengthen consensus by aligning miners’ interests with overall network security.
Handling Forks
When two miners find valid blocks at nearly the same time, a temporary fork occurs in the blockchain. The network handles this through temporary forks that resolve naturally, soft forks for backward-compatible protocol upgrades, and hard forks for protocol changes creating incompatible blockchains.
Bitcoin Network Security
Bitcoin’s security model protects against various network attacks by combining cryptographic techniques, economic incentives, and network effects.
Protection Against Common Attacks
The Bitcoin network is designed to resist several attack vectors and here is the brief overview of some of them:
Double-Spending Protection
The blockchain prevents spending the same Bitcoin twice by tracking all transaction history, with confirmed transactions becoming increasingly secure with each additional block.
51% Attacks
While an attacker controlling over 50% of network mining power could potentially reverse recent transactions, the enormous cost of acquiring sufficient hardware and electricity makes such attacks economically irrational, especially for transactions with multiple confirmations.
Sybil Attacks
Proof of Work prevents attackers from creating numerous fake nodes to influence the network, as computing power rather than node count determines mining influence.
Network Resilience
Bitcoin’s decentralized architecture creates several security advantages:
- No Single Point of Failure: Distributed nodes ensure the network continues functioning even if many nodes go offline
- Geographic Distribution: Nodes and miners spread across countries provide resistance against regional disruptions
- Open Source Verification: Transparent code allows continuous security auditing by the community
- Bug Bounties: Financial incentives for discovering and reporting vulnerabilities
Bitcoin Scalability and Decentralization Challenges
As Bitcoin has grown in popularity, it has faced significant challenges in scaling transaction capacity while also maintaining decentralization.
The Scalability Trilemma
Bitcoin, like most blockchain systems, confronts the “scalability trilemma“—the challenge of optimizing for scalability, decentralization, and security simultaneously, with improvements in any one area often coming at the cost of trade-offs in the others.
Block Size Limitations
Bitcoin’s 1MB block size limit creates a cap of approximately 7 transactions per second, competition for block space during high demand periods, rising transaction fees when network usage increases, but also enables reliable decentralization as smaller blocks are easier for nodes to process and store. This is a big challenge for network scaling without sacrificing Bitcoin’s decentralized nature.
Node Requirements
Running a full Bitcoin node requires 500+ GB of storage (growing continuously), sufficient bandwidth for transaction and block relay, processing power to verify transactions, and consistent uptime. These requirements have increased over time, potentially reducing the number of individuals able to run full nodes.
Layer 1 and Layer 2 Solutions
To address scalability challenges, the Bitcoin ecosystem has developed a two-layered approach to scaling.
Bitcoin Layer 1 (Base Layer)
Layer 1 refers to the Bitcoin blockchain itself—the main protocol where final settlement occurs. Layer 1 optimizations include:
SegWit (Segregated Witness)
Implemented in 2017, SegWit separated signature data from transaction data, effectively increased block capacity without changing the 1MB block size limit, and fixed transaction malleability.
Schnorr Signatures & Taproot
Activated in November 2021, these upgrades enabled more efficient multi-signature transactions, improved privacy for complex transactions, and enhanced smart contract capabilities.
Layer 2 Solutions
Layer 2 solutions build on top of the Bitcoin blockchain, moving some transactions off-chain while using the main blockchain for final settlement:
Lightning Network
- Payment channel network enabling instant, low-fee transactions
- Channels allow unlimited transactions between parties without recording each one on the blockchain
- Only channel opening and closing transactions need to be recorded on-chain
- Enables micropayments and higher transaction throughput
Sidechains
Separate blockchains pegged to Bitcoin that allow different consensus rules while maintaining a connection to Bitcoin’s security, such as Liquid Network and RSK (Rootstock).
State Channels
Similar to Lightning but designed for more complex interactions, enabling off-chain smart contracts and applications.
These Layer 2 solutions offer a way to scale Bitcoin transactions while maintaining the security and decentralization benefits of the core protocol.
Bitcoin Economic Incentives
Bitcoin’s system design incorporates economic incentives that align participants’ self-interest with the network’s security and functionality.
Mining Rewards
The primary economic incentives in Bitcoin come through mining rewards:
Block Subsidy
- New Bitcoins created with each block
- Started at 50 BTC per block in 2009
- Halves approximately every four years (210,000 blocks)
- The current reward is 3.125 BTC per block (as of April 2024 halving)
- Will continue halving until approximately 2140, when all 21 million Bitcoins have been issued
Transaction Fees
Additional fees paid by users to prioritize their transactions vary based on network demand and transaction size. As block subsidy decreases, these fees will eventually become the primary revenue source for miners.
Long-term Sustainability
As block rewards diminish over time due to halving, Bitcoin’s economic model shifts toward increasing value, potentially offsetting the decreasing quantity of rewards. Transaction fees gain importance for miner revenue, and a security budget transitions from primarily inflation-based to primarily fee-based.
Bitcoin Future Developments
Bitcoin continues to evolve through careful, deliberate improvements to its protocol and ecosystem.
Protocol Upgrades
Several potential system upgrades are under discussion or development. Here is an overview of some of them:
Drivechain
A two-way pegged sidechain proposal would allow Bitcoin to move between the main chain and various sidechains. It enables experimentation with new features while maintaining its security.
Stratum V2
Next-generation mining protocol that increases security and efficiency in mining operations while improving decentralization by giving individual miners more control.
Covenants
Script-level restrictions on how Bitcoins can be spent in the future. This would enable more complex smart contracts and security features through proposals like OP_CHECKTEMPLATEVERIFY and OP_TXHASH.
Research Areas
Ongoing Bitcoin research focuses on several key areas:
- Scalability Improvements: Continued work on transaction efficiency, blockchain growth rate reduction, and Lightning Network enhancements
- Privacy Enhancements: Techniques to improve transaction privacy, CoinJoin implementations, and zero-knowledge proof applications
- Quantum Resistance: Preparing for potential quantum computing threats through quantum-resistant signature schemes
These developments are trying to enhance Bitcoin’s capabilities while preserving its core properties of security, decentralization, and censorship resistance.
Conclusion
Bitcoin’s system combines multiple components to create a decentralized financial network unlike anything that came before it. From the open-source software and protocol rules to the global network of nodes and miners, each element plays a crucial role in maintaining Bitcoin’s security, transparency, and reliability.
What makes Bitcoin truly remarkable is how these components work together – cryptography secures transactions, mining creates new coins and validates blocks, nodes enforce the rules, and economic incentives align everyone’s interests. This carefully balanced system has withstood over a decade of scrutiny, attacks, and growing pains.
As Bitcoin continues to evolve, the core challenge remains finding ways to increase scalability without sacrificing decentralization or security. Layer 2 solutions like Lightning Network show promising ways forward, while ongoing research into privacy and quantum resistance aims to strengthen Bitcoin against future threats.
FAQs
What is the Bitcoin protocol?
It is the set of rules that govern how the Bitcoin network operates. It defines everything from the maximum supply of Bitcoins (21 million) to how transactions are validated and recorded. These rules are implemented in software code rather than as a separate document, ensuring they are enforced programmatically across the entire network.
What role do nodes play in the Bitcoin network?
Nodes are computers running Bitcoin software that form the backbone of the network. They have several functions, like storing and validating the blockchain, verifying transactions against Bitcoin's rules, relaying valid transactions and blocks to other nodes, rejecting invalid ones, and maintaining network decentralization.
How does mining secure the Bitcoin network?
The key here is the Proof of Work mechanism, which requires miners to expend significant computational resources to create valid blocks. This makes it economically costly to attack the network. The competitive mining process distributes block creation across multiple participants, preventing centralized control, while the immutable chain of blocks makes it exponentially more difficult to alter past transactions.
What is a Bitcoin wallet?
A Bitcoin wallet is software or hardware that stores the cryptographic keys needed to access and manage Bitcoins. Despite the name, wallets don't actually store Bitcoins—they store the private keys that prove ownership of Bitcoins recorded on the blockchain. Wallets allow users to generate Bitcoin addresses, sign transactions, view transaction history, and manage multiple addresses and keys.
What challenges does Bitcoin face in terms of scalability?
Challenges can be limited transactions due to block size constraints, increasing storage requirements for running full nodes, rising transaction fees during periods of high demand, and the “scalability trilemma” of balancing increased capacity with security and decentralization. These challenges have led to the development of various on-chain improvements and Layer 2 solutions.