Join Our Telegram channel to stay up to date on breaking news coverage
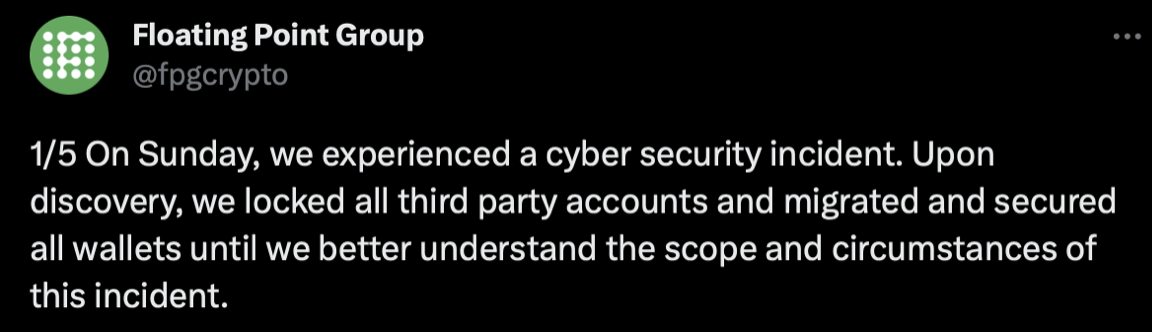
In light of the recent cyberattack, FPG’s trading activities, deposits, and withdrawals have been suspended as a precautionary measure. The firm is actively cooperating with law enforcement agencies, regulators, and Chainalysis to unravel the events leading to the breach and to initiate the asset recovery process.
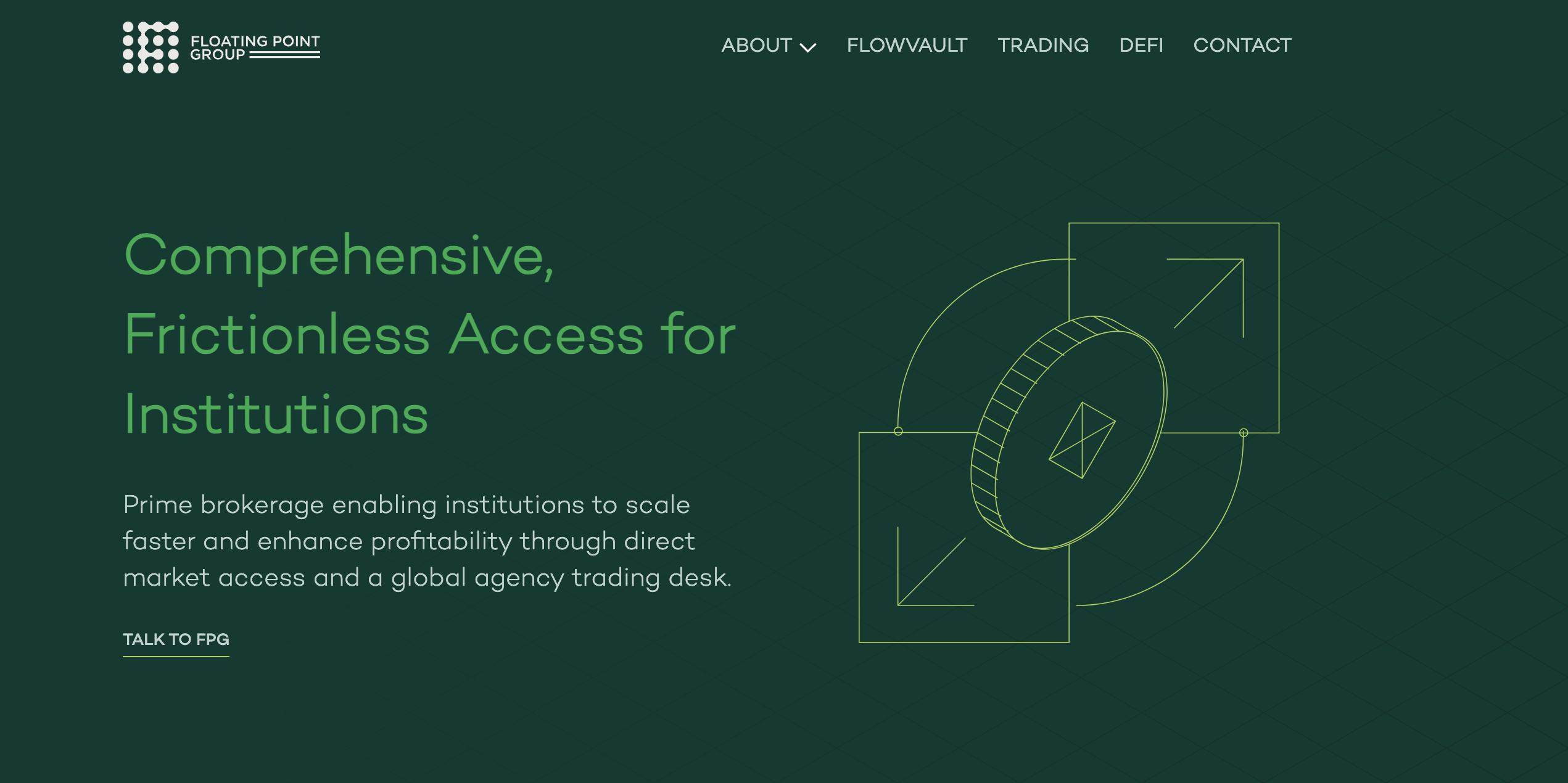
FPG Halts Trading and Seeks Recovery Following Cyberattack
Floating Point Group (FPG), an institutional trading desk specializing in cryptocurrencies, experienced a significant setback on June 11 when it fell victim to a cyberattack. This unfortunate incident has compelled the firm to suspend trading activities, as well as deposits and withdrawals on its platform.
FPG estimates that the attack resulted in a substantial loss of funds, ranging between $15 million and $20 million.
In response to the breach, FPG promptly took action by securing all wallets and locking third-party accounts upon discovering the security breach. The firm then decided to halt trading, deposits, and withdrawals as a precautionary measure. Fortunately, FPG’s implementation of account segregation mitigated the overall impact of the attack.
FPG is an international brokerage firm catering to institutional clients seeking access to crypto markets and manages a substantial $50 billion in assets, as stated on its website. However, this recent incident is likely to undermine institutional confidence in the crypto sector, which has already faced challenges due to market fluctuations and growing regulatory scrutiny.
To address the situation, FPG has been collaborating with various entities, including the FBI, the Department of Homeland Security, regulators, and Chainalysis, in an effort to comprehend the circumstances surrounding the attack and to recover the lost assets. However, due to the ongoing investigation and collaboration with law enforcement agencies, FPG is unable to disclose further details publicly.
FPG had previously taken significant precautions to safeguard its operations, engaging external auditors in December last year to conduct rigorous cybersecurity audits and penetration testing, which ultimately led to the attainment of the SOC 2 certification.
Developments In Atomic Wallet Hack Point Towards North Korea
FPG wasn’t the only victim of a cyber attack, as Atomic wallet made persistent headlines last week, reporting a loss of close to a million dollars in funds. While there was no clarity surrounding the hacker, a recent development points in the direction of North Korea.
Blockchain analytics firm Elliptic revealed today that the cybercriminal group believed to be associated with North Korea, known as Lazarus Group, has now accumulated over $100 million in stolen cryptocurrency from the recent attack on Atomic Wallet.
The breach, which occurred on June 3, initially resulted in the theft of digital tokens valued at $35 million.
Elliptic, attributing the attack to Lazarus Group, highlighted that this cybercrime syndicate has an extensive track record, having pilfered more than $2 billion through its prolific hacking activities. In a blog post on Tuesday, Elliptic expressed concern over the significant increase in the amount stolen, emphasizing that Atomic Wallet has yet to provide an explanation to its customers.
Atomic Wallet, an Estonia-based platform that enables users to store cryptocurrencies such as Bitcoin and Ethereum, last mentioned the hack on June 7 when it announced its collaboration with blockchain analytics firm Chainalysis to track the stolen funds. However, there has been no further communication from the Atomic Wallet team on its Twitter account since that tweet.
Elliptic confirmed that it has taken action to freeze the stolen funds, collaborating with investigators and exchanges worldwide to accomplish this. As a result, over $1 million worth of stolen assets have been successfully frozen. The firm also highlighted that the hackers have started utilizing Garantex, a Russian crypto exchange under sanctions, to launder the stolen assets.
Lazarus Group gained notoriety in the past when the U.S. Treasury Department sanctioned the coin mixing app Tornado Cash, citing its use by criminal entities, including state-sponsored hacking groups such as Lazarus Group, for money laundering purposes.
The group has been implicated in several high-profile attacks, including the $100 million Harmony Bridge hack in June 2022 and the $190 million Nomad bridge hack a month later.
In December of the previous year, it was reported that the Lazarus Group had pretended to be a venture capital firm in order to distribute malware. Cybersecurity company Kaspersky, in their report, referred to the Lazarus Group as BlueNoroff and revealed that the group had created many fake websites imitating venture capital companies and banks.
Related Articles
- Cryptocurrency Hacks Show Decline and Changing Dynamics – Insights from TRM Labs
- Crypto Funds 50% Of North Korean Nukes: Report
Join Our Telegram channel to stay up to date on breaking news coverage