Join Our Telegram channel to stay up to date on breaking news coverage
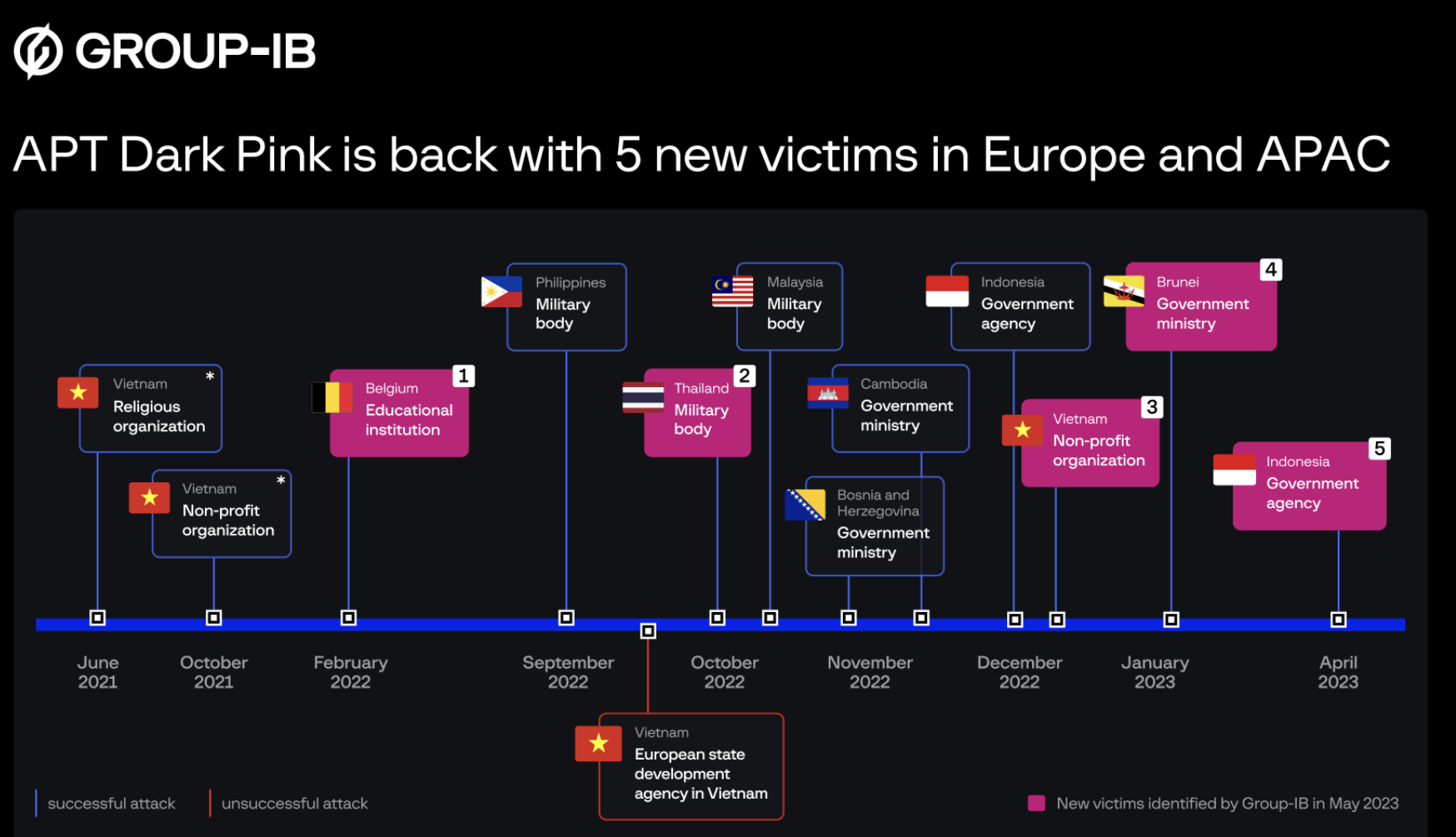
State-backed hackers are back on the prowl and are striking boldly as they have increased their caliber of victims. Known as Dark Pink, this hacking group, which has been suspected of having ties with an Asian government, has now started to attack government agencies in Brunie and Indonesia. The list of victims also includes a military body in Thailand, an educational institution in Belgium, and a non-profit organization in Vietnam.
Hacking on the Rise as Government’s Sensitive Data Become a Target
Government or government-tied organizations have always been primary targets of all major hacking attempts due to the sensitive nature of the information they hold.
And State-backed hackers, encouraged by the lack of regulatory red tape and abundance of government-aided tools, are not afraid to go head first, going as far as implementing brute force attacks to cripple the systems and attempting to steal data while agencies attempt restoration.
The biggest threat among them is phishing emails, one of the two tools used by Dark Pink in order to target agencies and steal their data. Phishing emails, according to IBM’s security threat index, comprise nearly one-third of all global attacks. Masquerading as legitimate government emails, these attacks bypass traditional security measures to install malware in victims’ systems successfully.
And because of these attacks’ insidious nature, Yahoo Finance reported that none of the government agencies responded to its emails for comments.
Group IB has reported that Dark Pink uses a custom toolkit in its spear-phishing emails to exfiltrate files and messenger data from infected devices and networks. The group has stated that Dark Pink has evolved these tools to bypass the defense mechanisms of cybersecurity systems.
One such example is the KamikakaBot module, a tool designed to read and execute commands from hackers via Telegram. While it was originally only stored in the file systems of infected devices, it has now divided itself into two parts – one controls the device, and the other steals the data.
Dark Pink is Not a One-Time Campaign – Group IB Malware Analyst
Analyzing the recent spree of attacks by Dark Pink, Andrey Polovinkin, a malware analyst working in Group IB, said that there is a large evidence hinting at the fact that Dark Pink is not only a one-time campaign being carried out by a known APT group but an evolving threat.
Referring to the persistent and unrelenting nature of the threats, which are often sponsored by the government, Andrey said, “The risk of highly damaging confidential data leaks remains alarmingly high.”
There are no clues about the original identity of Dark Pink as of right now. However, the sophistication behind their attacks indicates that they could be hailing from the Asia-Pacific region, as these regions have been ramping up their technologies when it comes to international espionage and cyber attacks.
One of these attacks includes building malware right into a Word file that, once downloaded, installs a RAT (Remote Access Trojan) on the victim’s systems, feeding the hacker every information about every click and every interaction that the victim’s system is engaged in.
State-Backed Hackers Have Been Making News Since 2021
Group IB reported that Dark Pink began their hacking campaign back in June 2021, during which they stole documents and recorded audio from infected devices.
The report also outlines the SideWinder APT activity between June and November 2021. Also known as Rattlesnake, Hardcore Nationalist (HN2), and T-APT-4, this hacking group attempted to hack a dozen of Asia-Pacific countries over a period of six months.
The highlights showed that there are four countries where SideWinder carried out its phishing campaign – Afghanistan, Bhutan, Nepal, and Sri Lanka. Group IB has also attributed the 2020 attacks on the Maldivian government to this particular group.
Another interesting detail that the report showed was Telegram was the channel used by SideWinder to review the results of their Malware’s commands.
From the Philippines to Cambodia, These Hackers Are Choosing Targets Based on Geo-Political Motivations
Researchers from DAS-Security, a Zhiejiang-based firm, have reported that the same group – Dark Pink – was responsible for attacking the Phillippine Military. Cambodia’s economy and finance ministry and Indonesia’s foreign ministry were also attacked by this group of attackers.
Due to the nature and the location of these attacks, DAS-Security has said that these attacks are geopolitically motivated. “This group has been particularly eyeing the Association of Southeast Asian Nation countries’ military and foreign ministry department,” DAS-security reported in its February report.
Dark Pink is Just One Of the Many Hacking Groups
The recent slew of hacking on government bodies has revealed that Dark Pink is not the only group carrying out its nefarious deeds. The current geopolitical climate is particularly volatile, and countries may be attempting to outcompete each other by attacking their competitor’s technological infrastructure.
One such name to have come up in this matter is Volt Typhoon. This Chinese hacking team, and a few others, have been blamed for orchestrating cyberattacks on US critical infrastructure, including transportation and telecommunication hubs.
Western intelligence agencies have dubbed Volt Typhoon as the biggest Chinese cyber-espionage campaign against the US government as part of the US disinformation campaign.
Backdoordiplomacy is another group to have been identified by Palo Alto Networks with links to the Chinese state government. According to Palo Alto, this group has been responsible for carrying out several intrusions against the Kenyan government over the past few years.
Related Articles
- How to Buy Bitcoin Safely?
- A Guide to Safely Buy Cryptocurrencies
- Russia No Longer Trying to Create a State-Run Cryptocurrency Exchange
Best Wallet - Diversify Your Crypto Portfolio
- Easy to Use, Feature-Driven Crypto Wallet
- Get Early Access to Upcoming Token ICOs
- Multi-Chain, Multi-Wallet, Non-Custodial
- Now On App Store, Google Play
- Stake To Earn Native Token $BEST
- 250,000+ Monthly Active Users
Join Our Telegram channel to stay up to date on breaking news coverage