One of the greatest drivers of the cryptocurrency industry’s success is its ability to build trust through code. Unlike traditional finance, which relies on trust in centralized third parties like banks and other institutions, cryptocurrency depends on innovative cryptographic systems that provide security and transparency without the need for untrustworthy intermediates.
Public and private keys are at the heart of the cryptography that powers blockchains. Thanks to these kinds of keys, anyone anywhere can send and receive cryptocurrency transparently. They are the foundation of blockchain technology.
This system allows crypto users to prove ownership of their coins, sign transactions, and keep their holdings secure without ever revealing sensitive information. In other words, keys make crypto “trustless” and eliminate the need for a middleman.
What Are Public and Private Keys in Crypto?
Public and private keys are a pair of cryptographic codes that work together. Think of them as a lock and key. One of them locks your crypto, the other one unlocks it.
The public key is similar to your email address. You can share it with anyone, and you must share it for so that others can send you crypto.
The private key is like your email password. You must keep it a secret as it is used to prove that you are the owner of the crypto wallet. If anyone gets their hands on your private key, they can access your wallet and drain it in seconds.
Here is a quick comparison to make things clearer:
| Feature | Public Key | Private Key |
| Can you share it? | Yes | No |
| What is it used for? | Receiving cryptocurrency and verifying a signature | Signing transactions and proving ownership |
| Who sees it? | Anyone | Only the crypto owner |
| What does it generate? | Crypto addresses | Public key |
Let’s say that you want to receive Bitcoin (or any other coin, for that matter). Your crypto wallet will give you a public address, which is derived from your public key. You need to give that address to the sender so that they know which wallet it transfer the coins to.
Now, let’s say that you want to spend Bitcoin. Your wallet uses your corresponding private key to sign the transaction. This is how you prove you are the real owner of the BTC in your wallet, which is why you can never share your private key. Once you sign the transaction, the network will use your public key to verify the digital signature and confirm that the transaction is valid.

If someone somehow gets your private key, they can easily move your crypto. That’s why you must keep it safe (offline, in cold storage, or in a secure hardware wallet).
Asymmetric vs. Symmetric Key Cryptography
You will often hear the terms asymmetric and symmetric encryption when learning about cryptography. They both involve keys but function in very different ways. This is where things get a little technical. Here’s a breakdown of the two:
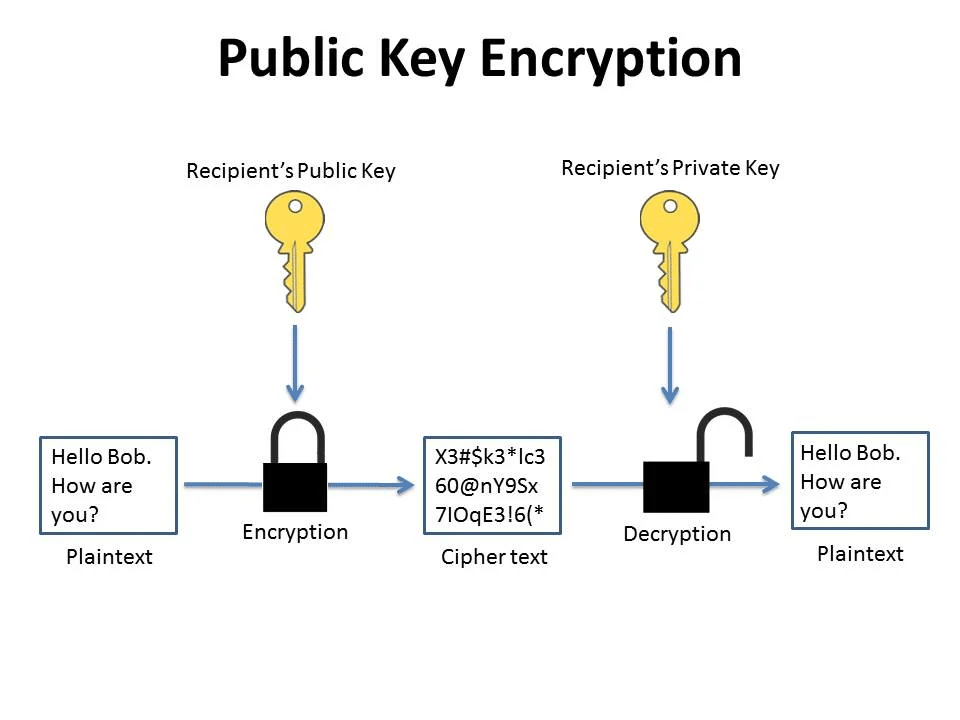
- Asymmetric key cryptography uses two keys: a public key and a private key. The public key encrypts messages, and the private key decrypts them. This setup allows secure communication without ever needing to share your private key.
- Symmetric key cryptography uses only one key for both encryption and decryption. Everyone involved needs access to the same key, which makes it less practical for open networks like blockchains.
Cryptocurrencies all use asymmetric encryption, which is also known as public key cryptography.
Note: The term private key encryption can sometimes refer to symmetric encryption, where just one shared key does everything. This can make it a bit confusing, but in crypto, we are always talking about asymmetric encryption.
Why Is Public and Private Key Encryption So Important?
Public and private key encryption isn’t just some background tech that only developers need to know about. It is an essential technology that forms the foundation of secure communications in the modern world. Without it, your crypto wallet wouldn’t be secure or transparent. Crypto is far from the only use case for this kind of cryptography. It is essential in secure email communication and safe internet browsing (like for online banking) as well.
This encryption method gives people the power to prove their identity and send information without fear of it being intercepted. Crucially, they don’t need to share their private key to do so safely, which helps keep their information and assets secure.
Public and Private Key Use Cases
Here are some of the most important ways key cryptography is used these days:
1. Cryptocurrency
Cryptocurrency is the most well-known use of key cryptography today. Public and private keys enable users to send and receive crypto securely. The public keys generate the wallet addresses, and the private keys are used to sign transactions and prove ownership.
If you lose your private key or it falls into the hands of a bad actor, you lose your crypto. It’s that simple.
2. Digital signatures
Digital signatures prove that a file or a message comes from a specific source (or a person). They are used in smart contracts, document verification, and software updates.
For instance, when a developer signs a software update, users can confirm its authenticity using the developer’s public key.
3. Email encryption
Services like ProtonMail and PGP (Pretty Good Privacy) use public and private keys to secure emails. The public key encrypts the email someone sends, and it can only be decrypted using the recipient’s private key. This means that only the recipient can read the email. Even the email provider can’t access it.
4. VPNs (Virtual Private Networks)
VPNs often use public key encryption to secure the connection between a device and its servers. This helps them establish secure communications, also known as a secure tunnel, so no one can snoop on users’ online activity.
5. HTTPS/ Secure websites
When you see the padlock in the top left corner of your browser, it means that the website is using SSL/TLS encryption. These encryption methods rely on public and private keys. The website uses a private key to prove it is legit, and the browser uses the public key to start a secure connection. This keeps your passwords, credit card numbers, and messages private from prying eyes.
Pros and Cons of Public-Private Key Encryption
Like any technology, public-private key encryption has its strengths and its limitations.
Pros:
- Strong security: Only the private key can unlock the encrypted messages created by the public key.
- No need to share private information: This offers secure communications without the need to give away your secret key.
- Proof of ownership and identity: Great for signing documents and transactions. You can easily prove something is yours or came from you.
- Used in open networks: Ideal for crypto and the internet, without the need for a central authority.
- Easy scaling: Public keys can be shared openly, so this works even with millions of users.
Cons:
- Losing your private key is devastating: If you lose your private key, there is no way to recover your crypto or data.
- Can be slow: Asymmetric encryption takes more computational power than symmetric cryptography.
- Key management is trickier: Users have to store and protect their private keys. Not everyone does this well.
- Can still be hacked if not handled properly. Poor key storage (like saving your key in a text file) makes it vulnerable.
The Role of Public and Private Keys in Crypto
In cryptocurrency, your private and public keys are everything. They don’t just help you secure your cryptocurrency wallet. They are your wallet, and the wallet would be worthless without them.
How Keys Work
When you create a crypto wallet, it will generate a private key. This is a long, random number. Using that number, the wallet will create a corresponding public key, and then a wallet address (usually a hashed version of the public key).
Once your wallet is generated, you can start using it. Here’s what happens next:
- You share the wallet address or your public key to receive funds
- To send funds, your wallet signs the transaction using your private keys
- The network verifies this signature using your public key. If it checks out, the transaction is confirmed.
Why It’s Important
There are three main reasons why keys are important in crypto:
- Security: There is no password reset in crypto. Your private key is the only proof that the wallet is yours. Lose it, and your access to it is gone forever.
- Trustless system: There is no central authority in crypto. Keys let the system run on code and math. There are no people or middlemen.
- Ownership: Whoever holds the private key controls the crypto in a wallet. This is where the saying comes from: “not your keys, not your coins.”
How to Keep Your Private Keys Secure
The private key is the most sensitive part of any crypto setup. If someone else gains access to it, they can move your funds without any questions asked. Here are some essential tips to help you keep your private key and wallet secure:
1. Use a Hardware Wallet
A hardware wallet will store your private key offline. This means that hackers can’t access it even if your computer or phone has been compromised.
Popular options for hardware wallets include Ledger and Trezor. A hardware wallet won’t expose your private key to the internet, not even when you are sending crypto.

Hardware wallets are generally secure, but vulnerabilities can still occur. In December 2023, for instance, Ledger experienced a significant security breach. A hacker accessed the NPMJS account of a former Ledger employee using a phishing attack, which, for a while, led to concerns about the safety of digital assets stored on Ledger devices.
Attackers injected malicious code into the library, which was then unknowingly adopted by several decentralized applications like SushiSwap and OpenSea. The result was unauthorized draining of users’ crypto wallets with the total losses estimated at around $600,000.
In response, Ledger updated the compromised library and removed the malicious code. They also pledged to reimburse all affected users, which they did by the end of February 2024.
Ledger has been a major target for hackers for many years, mostly because it is such a popular brand of hardware wallet. However, Ledger has generally done a good job of keeping wallets secure and has been transparent about the attacks over the years, which is why it’s considered one of the safest hardware wallets today.
This breach affected our customers’ contact details, mostly email addresses.
No payment information, no credentials, no crypto funds were concerned.
Your funds are safe and have not been compromised. You are the only in control of your crypto.
— Ledger (@Ledger) July 29, 2020
2. Write It Down (and Store It Safely)
If your wallet gives you a recovery phrase, you must keep it as secure as possible. This phrase acts as a master key that can restore your entire wallet, including all private keys and wallet addresses. Some try to memorize it to avoid the risks of having it written down, but the risk of forgetting it is often higher than the risk of theft. Avoid taking a photo with your phone or storing it with a cloud service, as your phone could be accessed by phishing or social engineering attacks.
Ideally you should:
- Keep your written note in a fireproof safe
- Don’t share the note with anyone
- Don’t store it on your phone or PC
Some experts even suggest keeping the phrase in multiple secure locations in case of natural disasters. Storing your phrase improperly can lead to irreversible loss. Mark Frauenfelder, a journalist and crypto enthusiast, lost access to his $30,000 worth of Bitcoin after he misplaced the paper containing his recovery phrase and PIN. Unlike in traditional finance, there is no customer support team that can get your crypto back.
3. Avoid Copy-Pasting Private Keys
Typing or pasting your private key into any website or app is dangerous. There are many malicious programs that can easily steal it if it manages to infect your device. Legit wallets will never ask you to enter your private key unless you are restoring access.
If you are asked to provide the private key, always double-check the source before you take action. Make sure the domain name of the wallet provider is correct and bookmark the correct homepage to avoid clicking on scam websites.
4. Use Encrypted Backup Tools
If you really need to go digital to store your keys, make sure to take additional measures for security. You can use encrypted storage like Bitwarden, 1Password, or an air-gapped USB drive. Unless it is absolutely necessary, make sure it is never connected to the internet.
5. Be Careful with Who You Trust
Scammers often trick users into handing over their keys willingly. Remember the following:
- People only need the recipient’s public key to send crypto. No one who wants to send you crypto needs your private key.
- You should never share your private key with anyone, not even support teams. No legitimate support team will ask you for your private key or recovery phrase.
In 2025, there has been a surge in violent abductions and ransom demands targeting cryptocurrency holders, especially in the United States and France. These are known as “wrench attacks.” The crimes involve physical coercion to obtain cryptocurrency wallets and funds. While digital security is important, your physical security is more important. If possible, don’t publicize your crypto holdings whatsoever, especially if you have a large portfolio.
6. Use Strong and Unique Passwords for Your Wallet
Using weak or reused passwords can seriously compromise your wallet’s security. A European crypto owner once lost access to his $3 million worth of Bitcoin because of a corrupted wallet file and a forgotten password. After several experts failed to help him, a hardware hacker discovered that his password was generated using a flawed version of a password manager, which made it predictable.
7. Consider Using Multi-Signature Wallets
Multi-signature wallets require more than one private key to authorize a transaction, which adds another layer of security. In a multi-sig setup, even if one of your private keys is lost or stolen, the funds will remain secure.
Why Keys Matter More Than Ever
Public and private keys are crucial for digital security, both in crypto and in the internet in general. Without them, everything from wallet access to encrypted messages would be wide open to attack.
Your private key is your master password. If someone gets their hands on it, your funds and data will be gone before you know it. This is why protecting it is non-negotiable. Whether you are investing in cryptocurrencies or just sending an email containing sensitive data, this form of cryptography ensures that the data reaches only the intended recipient.
From digital signatures to encrypted VPN tunnels, the use of keys goes beyond crypto. However, they are nowhere more vital than in the world of blockchain.
FAQs
What's the difference between a public and private key?
A public key is something you can share with anyone. A private key is what you keep to yourself. You use the private key to unlock or sign messages and transactions that were encrypted with the public key.
Why is it important to keep my private key safe?
If someone gets access to your private key, they can access your crypto wallet or decrypt data. There is no undo button.
What is asymmetric encryption?
Asymmetric encryption is a system where two different keys are used - a public one to encrypt and a corresponding private key to decrypt.
Is public-private key encryption only used in crypto?
Not at all. It is also used in email security, secure websites, cryptography for digital signatures, VPNs, and more. Crypto just happens to be where it gets the most attention.